vulnerability
Vulnerability:- Vulnerability in any system is the result of an intentional or unintentional omission or of an inadvertent design mistake that directly or indirectly leads to a compromise in the system’s availability, integrity, or confidentiality. In information assurance, vulnerabilities may hide in each level of security, be it information access security, computer and storage security, communications security, or operational and physical security. In the case of information systems, the major components are people, hardware, and software. Therefore, the presence of vulnerabilities must be sought in each of these three areas.
Picture 1 illustrates the factors that contribute to a secure cyberspace and the expectations out of cyber security. Over half a century ago, designers, engineers, and scientists successfully quantified the concept of reliability for the design and maintenance of hardware and of software to a lesser extent.
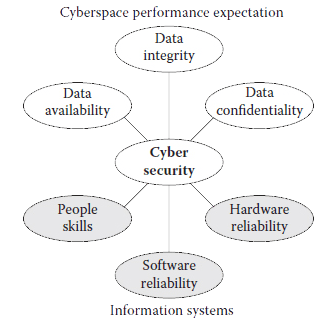
vulnerability
Today, efforts are being made to quantify the abstract concept of vulnerability as it applies to the security of information systems. The aim is to express the perceived level of security in a way that is measurable, standardized, and understood and to improve “the measure ability of security through enumerating baseline security data, providing standardized languages as means for accurately communicating the information, and encouraging the sharing of the information with users by developing repositories”. Vulnerabilities can be hidden in data, code, and most often in processes that inadvertently allow unauthorized access. Intrusions, however, can occur not only in the Internet, but also in the intranets, where most often security is not as strong. Security can be strengthened through intelligent mechanisms of authentication applied at both ends the user side as well as the server side.
At the user side, authentication can be greatly fortified with the introduction of additional mechanisms, such as one-time passwords (OTP), provided via intra- or extra-Internet channels. Such channels can be biometrics, questionnaires, or additional transparent parameters related to the user device identification numbers, such as manufacturer’s serial number, Media Access Control (MAC), or International Mobile Equipment Identity (IMEI). MAC, also referred to as Physical Address, is a 48-bit number,
expressed as 12 hexadecimal digits, that uniquely identifies the network interface of the computer. The network interface circuit may be an insert able network card or may be embedded in the computer’s motherboard. Picture 2 shows how the MAC address of a personal computer can be identified. IMEI similarly uniquely identifies devices that utilize mobile telephony and is a number, usually 13 to 15 digits long. Mobile telephony providers assign a telephone number to devices linking them to their IMEI identification.
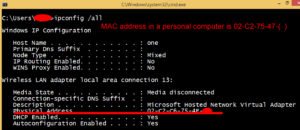
Picture 3 illustrates the IMEI numbers available inside mobile phones. In addition to the available MAC and IMEI numbers, device serial numbers and network parameters can also be used for authentication, such as intranet and Internet addresses. The above apply to client authentication toward the server. At the server side, the use of certificates, IP restrictions, and data encapsulations can greatly enhance authentication and security. While in transit, data can be protected by hash codes, such as the cyclic redundancy code (CRC), and by the private key/public key encryption mechanisms. Vulnerabilities in information systems can originate in a very wide variety of causes, ranging from firewall penetrations and Trojan horse attacks to decentralization and static resource allocation. Most frequently, vulnerabilities are introduced while systems are being upgraded or adapted to new operational environments.

I hope that you understand my post. if you like this post then share my post, and comment on my post if you have any suggestion or Queries related to vulnerability. Thank you




