Penetration testing
Penetration testing, often called “pentesting”, “pen testing”, “network penetration testing” or “security testing”, is the practice of attacking your own or your clients’ IT systems in the same way a hacker would to identify security holes. Of course, you do this without actually harming the network. The person carrying out a penetration test is called a penetration tester or pentester. Penetration testing requires that you get permission from the person who owns the system. Otherwise, you would be hacking the system, which is illegal in most countries – and trust me, you don’t look good in an orange jump suit. The difference between penetration testing and hacking is whether you have the system owner’s permission. If you want to do a network penetration test on someone else’s system, we highly recommend that you get written permission. In this case, asking first is definitely better than apologizing later!
Ethics of a Penetration tester
Every penetration tester that works for the information security industry must have ethics that will help him to serve his client better and to avoid any illegal activities.Of course for this reason penetration testing companies are requiring from their penetration testers to sign the NDA (Non-disclosure agreement) in order to protect their clients and align with the current laws depending the location as the legal framework can be different from country to country. However the penetration tester must be aware of the current laws and must remain fully ethical and professional at all times as the information security industry is not that big and a potential mistake can mark your career.So according to my personal opinion the following are some of the ethical standards that a penetration tester must have:
Serve and protect the client and uphold the security profession
Never take personal copies of client’s data
Never perform unauthorized testing
Don’t discuss findings with unauthorized people
Don’t publish vulnerabilities without permission
Test everything in scope and never go outside
Observe all legal requirements
Act with integrity
Protect client’s data (encryption etc.)
Don’t associate with black-hat hackers
Types of Pen Testing
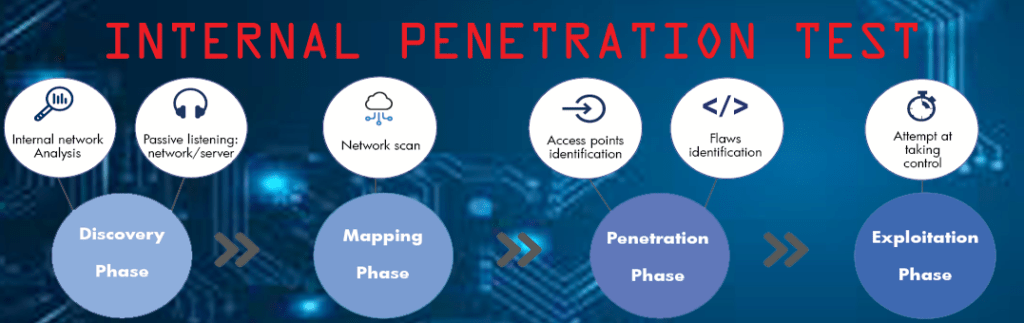
INTERNAL PENETRATION TEST
An Internal Penetration Test differs from a vulnerability assessment in that it actually exploits the vulnerabilities to determine what information is actually exposed. An Internal Penetration Test mimics the actions of an actual attacker exploiting weaknesses in network security without the usual dangers. This test examines internal IT systems for any weakness that could be used to disrupt the confidentiality, availability or integrity of the network, thereby allowing the organisation to address each weakness. Internal Penetration Test follows documented security testing methodologies which can include:
Internal Network Scanning
Port Scanning
System Fingerprinting
Services Probing
Exploit Research
Manual Vulnerability Testing and Verification
Manual Configuration Weakness Testing and Verification
Limited Application Layer Testing
Firewall and ACL Testing
Administrator Privileges Escalation Testing
Password Strength Testing
Network Equipment Security Controls Testing
Database Security Controls Testing
Internal Network Scan for Known Trojans
Third-Party/Vendor Security Configuration Testing
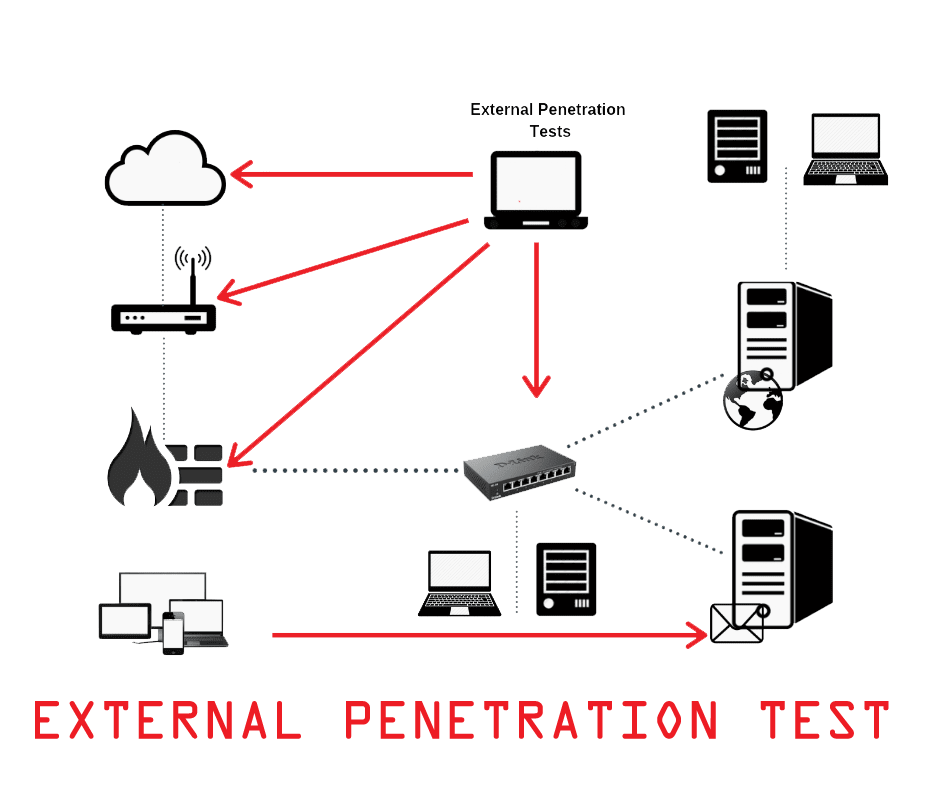
EXTERNAL PENETRATION TEST
An External Penetration Test differs from a vulnerability assessment in that it actually exploits the vulnerabilities to determine what information is actually exposed to the outside world. An External Penetration Test mimics the actions of an actual attacker exploiting weaknesses in the network security without the usual dangers. This test examines external IT systems for any weakness that could be used by an external attacker to disrupt the confidentiality, availability or integrity of the network, thereby allowing the organisation to address each weakness. External Penetration Test follows best practice in penetration testing methodologies which includes:
Footprinting
Public Information & Information Leakage
DNS Analysis & DNS Bruteforcing
Port Scanning
System Fingerprinting
Services Probing
Exploit Research
Manual Vulnerability Testing and Verification of Identified Vulnerabilities
Intrusion Detection/Prevention System Testing
Password Service Strength Testing
Remediation Retest (optional)
Following are the important types of pen testing −
Black Box Penetration Testing
White Box Penetration Testing
Grey Box Penetration Testing
Pen Testing
For better understanding, let us discuss each of them in detail −
Black Box Penetration Testing
In black box penetration testing, tester has no idea about the systems that he is going to test. He is interested to gather information about the target network or system. For example, in this testing, a tester only knows what should be the expected outcome and he does not know how the outcomes arrives. He does not examine any programming codes.
Advantages of Black Box Penetration Testing It has the following advantages −
Tester need not necessarily be an expert, as it does not demand specific language knowledge
Tester verifies contradictions in the actual system and the specifications
Test is generally conducted with the perspective of a user, not the designer
Disadvantages of Black Box Penetration Testing Its disadvantages are −
Particularly, these kinds of test cases are difficult to design.
Possibly, it is not worth, incase designer has already conducted a test case.
It does not conduct everything.
White Box Penetration Testing
This is a comprehensive testing, as tester has been provided with whole range of information about the systems and/or network such as Schema, Source code, OS details, IP address, etc. It is normally considered as a simulation of an attack by an internal source. It is also known as structural, glass box, clear box, and open box testing. White box penetration testing examines the code coverage and does data flow testing, path testing, loop testing, etc.
Advantages of White Box Penetration Testing It carries the following advantages −
It ensures that all independent paths of a module have been exercised.
It ensures that all logical decisions have been verified along with their true and false value.
It discovers the typographical errors and does syntax checking.
It finds the design errors that may have occurred because of the difference between logical flow of the program and the actual execution.
Grey Box Penetration Testing
In this type of testing, a tester usually provides partial or limited information about the internal details of the program of a system. It can be considered as an attack by an external hacker who had gained illegitimate access to an organization’s network infrastructure documents.
Advantages of Grey Box Penetration Testing It has the following advantages-
As the tester does not require the access of source code, it is non-intrusive and unbiased
As there is clear difference between a developer and a tester, so there is least risk of personal conflict
You don’t need to provide the internal information about the program functions and other operations
I hope that you understand my post. if you like this post then share my post, and comment on my post if you have any suggestion or Queries related to Penetration testing. Thank you!




